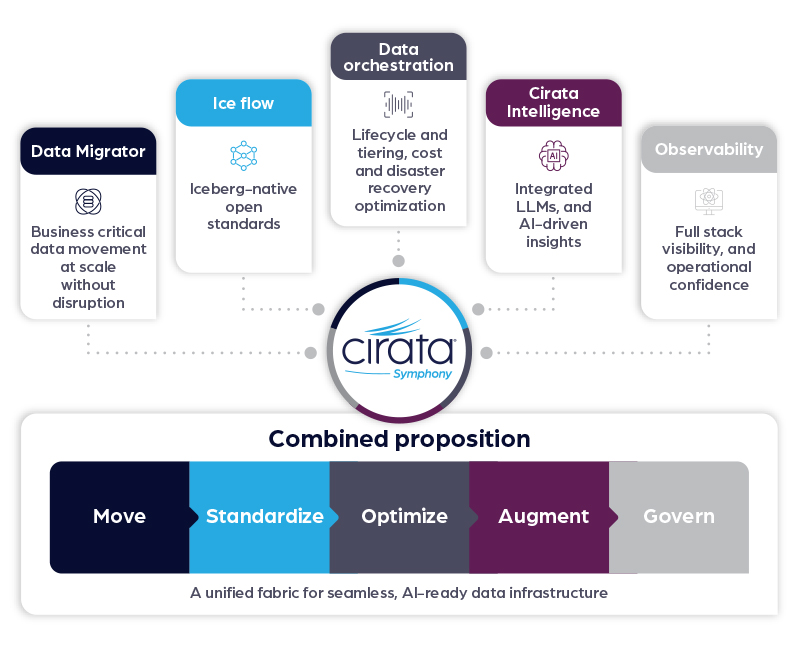
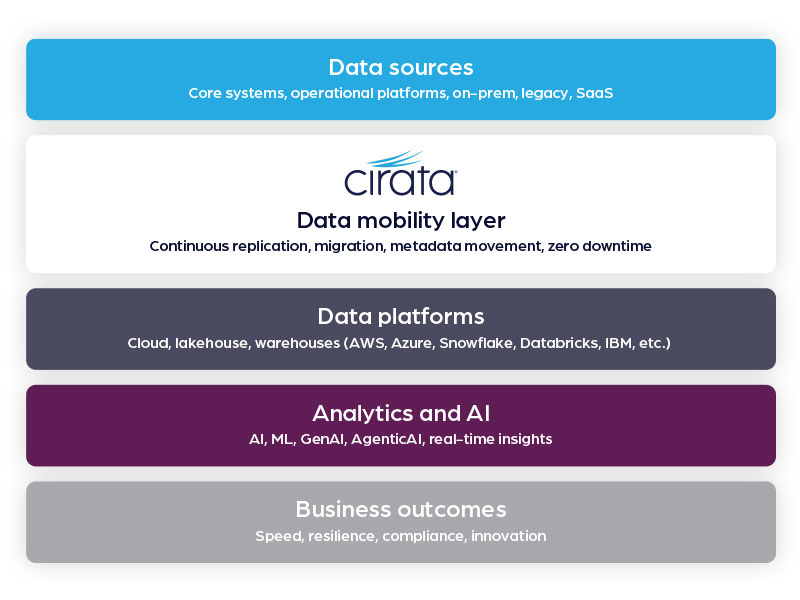
Built for the moments that matter most to your data
Data strategies didn't fail – the world changed. Cirata exists because downtime-based data movement no longer scales.

Data modernization
Update legacy systems without risk
Move massive datasets from legacy platforms to modern cloud and data architectures without downtime, re-writes, or business disruption.
learn more
Risk management
Data resilience, built in
Continuously replicate and protect critical data to ensure rapid recovery, regulatory compliance, and uninterrupted operations.
learn more
AI enablement
AI starts with data that's ready
Remove data gravity and friction, while unifying and delivering live, high-quality data to AI platforms, all without disrupting production systems.
learn more